Some points to points to ponder
- An initial permutation P before round 1,and its inverse at the end
- Halves are swapped after last round
- A final permuatation(inverse of P) is applied to (R16,L16) to yield ciphertext
weak keys
- A weak key is the one which after parity drop operation,consists either of all 0's,all 1's or half 0's and half 1's
- Four out of the 256 keys are weak keys
- what the key scheduling algorithms does it just pemutates and shift operations
- so if we do with the shift operation and permutation for this bits it almost results the same.That means there is non-linearity in the key scheduling its just trasposition
- so these keys are considered as the weak keys
- If we encrypt a block with a weak key and subsequently encrypt the result with the same weak key,we get the original block
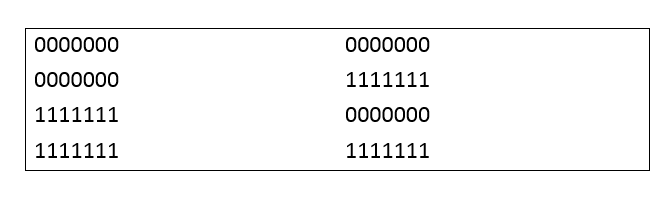
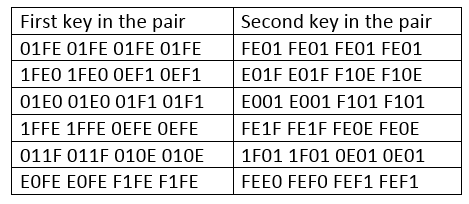
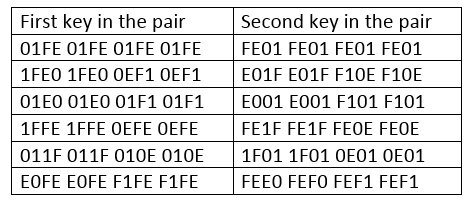
Semi weak keys
- A semi weak key creates only two different round keys and each of them is repeated eight times
- There are six key pairs that are called semi-weak keys
- The round keys created from each pair are the same in diffferent order
The main disadvantage of DES is the Key size because the key size is only 56 bits and this DES can be vulnerable to atacks and they can break the Key by Brute force attack.so in order to improve this they have deveoped 2-DES and 3-DES
- The major criticism against DES is the key length
- So,we may try cascading several DES applications
Multiple DES
2 DES
- Uses two applications of the DES cipher
- The total Key Size is 56 * 2 = 112 bits
- However 2 DES is vulnerable to a known Plaintext attack
- Attacker performs a known plaintext attack.He collects (P,C) pairs.
- Using 1st relation,he encrypts p using all possible 256 keys,and records all values for M
- Using 2ndrelation,he decryptes C using all possible 256 keys,and records all values for M
- M = Ek1(P) and M = Dk2(C)
- At some position the attacker will get the Plaintext
- So they extended there this 2-DES into Triple Des
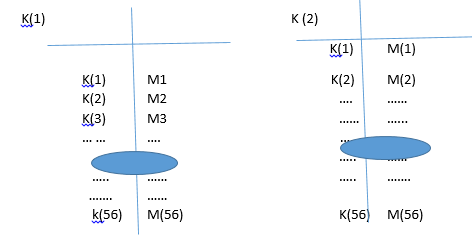
Triple DES(3 DES)
In cryptography,Triple DES is the common name for the Triple Data Encryption Algorithm(TDEA or Triple DEA) block cipher,which applies the Data encryption Standard(DES) cipher algorithm three times data block
The original DES cipher's key size of 56 bits was generally sufficient when that algorithm was designed,but the availability of increasing computational power made Brute Force Attacks feasible.Triple DES provides a relatively simple method of increasing the key size of DES to product against such attacks,with ut the need to design a completely new block algorithm
- Triple DES uses a "key bundle" which comprises three DES keys,K2,K2,K3,eah of 56 bits (excluding parity bits).The encryption algorithm is
- cipher text = EK3(DK2(EK1(plaintext)))
- DES encrypt with K1,DES decrypt with K2,then DES encrypt with k3
- Decryption is the reverse:
- plaintext = DK1(EK2(DK3(cipher text)))
- Decrypt with K3,encrypt with K2,then decrypt with K1
- Each triple encryption encrypts one block of 64 bits of data
- In each case the middle operation is the reverse of the first and last.This improves the strength of the algorithm when using Key option 2,and provides Backward Compatibility with DES with Keying option 3
- There are many keying options but usually use KEYs which are independent from one another to provide better security
- we can take K1 = K3,and K2 as different.Here the size of the key would be 112 bits and security will be less when compared to the different keys
- we can also take same keys K1,K2,K3, but it will be similar to the DES
- the most prefered option in 3-DES is to use 3 different indeendent keys
The next stage of 3-DES is AES
Advanced Encryption StandardBrute force attack
- In crytogrpahy a brute force attack is a cryptanalytic attack.
- It is used against any encrypted data.It comes into play when te atacker can't take advantage of other weakness in an encryption system(if any exist) that wuld make the task easier
- It consists of systematically checking all possible keys until the correct key is found
- In the worst case,this would involve traversing the entire search space